WE
Forebrook is a cybersecurity and IT governance
consulting services firm based in Dubai. We are
vendor independent and specialise in security
assessments, risk assessments,
design & review of ISMS,
and implementation of ISMS
processes. Our assessments include practical
recommendations and actionable advice, with
prioritised roadmaps to implement controls.
We also provide IT Infrastructure Services, IT
Asset Inventory, CMDB & Documentation
services, Cloud Services, virtual CIO and virtual CISO services.

Assessment Services
IT SECURITY ASSESSMENT
COMPLIANCE ASSESSMENTS
IT RISK ASSESSMENT
CLOUD SECURITY ASSESSMENT

INFRASTRUCTURE ASSESSMENT
VULNERABILITY ASSESSMENT
IT SECURITY AUDIT
IT HEALTH CHECK
IMPLEMENTATION & OTHER SERVICES
DOCUMENTATION
ISMS DESIGN, IMPLEMENTATION
DISASTER RECOVERY PLANNING & BCP
SECURITY AWARENESS WORKSHOPS

VIRTUAL CISO SERVICES
VIRTUAL CIO SERVICES
IT MANAGED SERVICES
CMDB DESIGN, IMPLEMENTATION

Microsoft Power Platform
In this fast-paced world, we understand the importance of being data-driven and task-based. Microsoft Power Platform is a one-stop end-to-end solution to automate processes and workflows. It’s a system that gives people the ability to evaluate, act, and automate on business-critical data. Microsoft’s Common Data Service is used by the Power Platform tools to manage your data. Our specialists will closely work with your team to tailor an app that perfectly suits your business needs.

Web Development
We offer full-cycle web development services. Much like architecture, web development, too, is about building and designing. From basic websites and web portals to extensive e-commerce and web applications, we work on it together. Our diverse team pools in ideas and with our collective experience in multiple industries, we provide you a solution tailored for your business. Our emphasis is on doing right from the start because a good foundation is key to a perfect building!

Office 365
In this fast-paced world, we understand the importance of being data-driven and task-based. Microsoft Power Platform is a one-stop end-to-end solution to automate processes and workflows. It’s a system that gives people the ability to evaluate, act, and automate on business-critical data. Microsoft’s Common Data Service is used by the Power Platform tools to manage your data. Our specialists will closely work with your team to tailor an app that perfectly suits your business needs.

Sharepoint
Sharepoint is based on the idea of streamlining activities of the employees and the business processes specific to your organization. Business teams can use SharePoint’s workflow apps, list databases, web parts, and security features to collaborate online. Not only does It allow collaboration but also ensures employee productivity. So whether you want support in developing a solution from the beginning, enhancing the current version, resolving issues, or to perform an assessment of your existing solutions, we are happily at your disposal.

Business Process: Mapping and Automation
Businesses nowadays are weighed down by a pile of repetitive tasks that are necessary to meet objectives. Business Process Mapping is the key to execute such projects in a timely manner, while also maintaining high quality and adhering to a set budget. Our experts will work closely with you to provide businesses viable options for enhancing efficiency and productivity. Organizations benefit from understanding their business processes better by using process mapping, but process automation integrates systems and machineries into rule-based procedures.

Payment Gateway Integration
If your main audience is online, it is essential to integrate payment gateway in your website. We can’t emphasize enough how a well-designed payment gateway will help smoothen transactions and eventually, contribute to the success of your business. Quick and user-friendly, our team will design custom payment solutions to cater your clients. We believe we do not just have a responsibility towards you but also your clients.
IT SECURITY ASSESSMENT
IT Security Assessments are indispensable
for the security information systems. In an
environment with existing security controls,
periodic assessments uncover gaps and
help improve the security posture. If an
ISMS is not in place, the best place to start
is to conduct a preliminary assessment to
identify applicable controls.
Our assessments are comprehensive and
we produce detailed and bespoke reports.

IT SECURITY ASSESSMENT
IT Security Assessments are indispensable
for the security information systems. In an
environment with existing security controls,
periodic assessments uncover gaps and
help improve the security posture. If an
ISMS is not in place, the best place to start
is to conduct a preliminary assessment to
identify applicable controls.
Our assessments are comprehensive and
we produce detailed and bespoke reports.

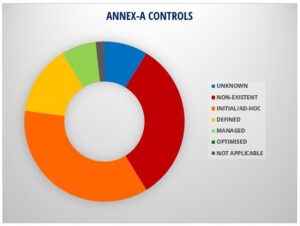
SECURITY STANDARDS, REGULATIONS
▪ UAE Information Assurance Regulation
▪ ADSIC
▪ NESA
▪ Dubai ISR
▪ ADHICS
▪ UAE DPL (Law No.45)
▪ CB UAE Regulations, Guidelines
▪ SAMA CyberSecurity Framework
▪ Oman CMA CyberSecurity Regulation








▪ ISO 27001:2013
▪ ISO 22301
▪ PCI-DSS v4
▪ HIPAA
▪ SWIFT v2022
▪ GDPR
IT RISK ASSESSMENT
This is a special kind of assessment where risks
related to information systems are identified,
classified and risk treatment options are investigated.
A risk register is created where risks related to each
information asset are recorded and risk response
strategy for each of the identified risks is defined.

An accurate risk-assessment is the
driving force of every security strategy.


CLOUD SECURITY ASSESSMENT
Organisations are rapidly moving to the cloud and
security of data and IT assets on the cloud is now
even more important than when resources and data
were on your premises.
We conduct a cloud security assessments to
identify the footprint, vulnerabilities and risks
associated with cloud infrastructures and
SaaS apps against CSA CCM 4.0. We also
conduct assessments against security best
practice documents by cloud service providers
such as Microsoft (Azure) or Amazon (AWS).

IT INFRASTRUCTURE ASSESSMENT
IT infrastructure assessment is required from time to
time as an input to decision making – for strategic
investments in technologies or for process
improvement and optimisation.
The outcome of such an assessment will be
detailed documentation, a dashboard of the
overall infrastructure, rich architecture diagrams,
identification of redundant systems and
recommendations to upgrade or replace.
These reports can be used as a starting
point to plan migration to the cloud.

VULNERABILITY ASSESSMENT
VA is an automated scan using tools to
identify attributes of hosts such as OS,
Applications, open ports and vulnerabilities of
these hosts
VA will help identify outdated software
versions, misconfigurations and critical
security issues.
Raw reports generated by the scanner will be
reviewed by an experienced security
consultant, who will prepare summaries and
course of action for remediation.

IT SECURITY AUDIT
An IT Security Audit is similar to other
assessments except that this is limited to
identifying gaps in the system and reporting the
same. Also, in this type of an assessment we rely
upon the company’s IT team and security officer
to provide data.
This is a useful service for internal auditors and
the management which seeks a third-party
assessment report of the as-is state.

IT HEALTH CHECK FOR SMEs
Organisations need to have a good understanding
of the IT environment and investigate whether IT is
delivering value to the business. Without an up-todate report of the existing environment, decisions
for upgrades may not be aligned with business.
Conduct a health check to take stock of your IT
environment and explore how new technologies
can be adopted and processes can be optimized.
Recommendations for improvement often result
in huge cost savings.

DOCUMENTATION
We believe that we are among the very few, if not
the only service provider in the region offering
documentation as a separate service.
If an organisation does not have current and
updated documentation, it is counted as a key risk
to information systems.
We create extensive documentation of
applications, infrastructures, processes and
procedures. We prepare manuals, architecture
diagrams, user-guides and SOPs.

ISMS DESIGN, IMPLEMENTATION
An ISMS is essential for organisations to manage and
monitor security; and to measure efficiency. Though a
number of controls and processes are in place by
necessity, many organisations do not have a formally
defined ISMS.
We can design an ISMS from scratch – such as
an ISMS conforming to ISO27001 or the NIST-CSF
and help you identify components that are
required but not implemented. We can create a
detailed roadmap to reach the desired state.

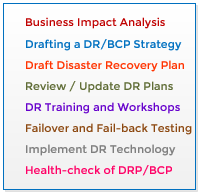
DISASTER RECOVERY PLANNING
It is essential for organisations to have a
comprehensive contingency plan in case of a
disaster – whether natural or man-made. A
continuity plan which can be invoked when a
disruption occurs. A BCP/DR plan should be
updated regularly and tested frequently for
readiness and efficacy.
We help you identify critical services,
business impact and draft a cost-optimized,
practical BCP and help you select
appropriate DR solutions.
USER AWARENESS WORKSHOPS
We conduct engaging and content rich
awareness workshops for different audience
in the organisation
▪ The Board and Top Management
▪ Executives and Managers
▪ Audit and Compliance Team
▪ Systems Team
▪ Application Team
▪ End-Users
▪ Security Team
We create relevant topics for each of these
groups and useful in their work.

VIRTUAL CISO SERVICES
There is a serious shortage of qualified security
professionals worldwide. If the United States has
700K positions open, the rest of the world is worse off.
Besides, highly qualified security professionals are
very expensive hires.
We can take care of your security needs for a
fraction of the cost you would pay a resident
CISO.
Contact us today for details on our
vCISO plans.
“With approximately 700,000 cybersecurity positions open, America faces a national security challenge that must be tackled aggressively.
Announcement of White House National Cyber Workforce and Education Summit JULY 18, 2022
VIRTUAL CIO SERVICES
Many organisations may not require a full-time
CIO and even those organisations with a CIO
may need to offload certain tasks from time to
time. Forebrook can assist your organisation by
performing some or all CIOtasks by drawing
from a pool of experienced professionals.
With Forebrook, you can avail the
services of senior consultants
for a fraction of the cost of hiring
highly experienced resources.

CLOUD SERVICES
We assist you in your cloud computing
strategy, by doing assessments, identifying
areas which can leverage cloud platforms,
identifying potential risks, undertaking
feasibility studies and computing total costs
of moving to the cloud – including hidden
costs – providing actionable intelligence to
decide on your strategy for a private, public or
hybrid cloud. We also manage resources on
Azure, AWS and MS-365 for our clients.

CMDB DESIGN, IMPLEMENTATION
Design a robust CMDB based on the ITSM
processes followed in the organisation or on a
standard/framework such as ITIL or ISO 20000.
We will review and update your CMDB and
implement a suitable tool for managing the
CMDB. A CMDB is essential for the following:
1. Application Mapping
2. Incident and Problem Management
3. Monitoring
4. Root Cause Analysis
5. Impact Analysis
6. Data Center Relocation/Consolidation


NEWS 2022

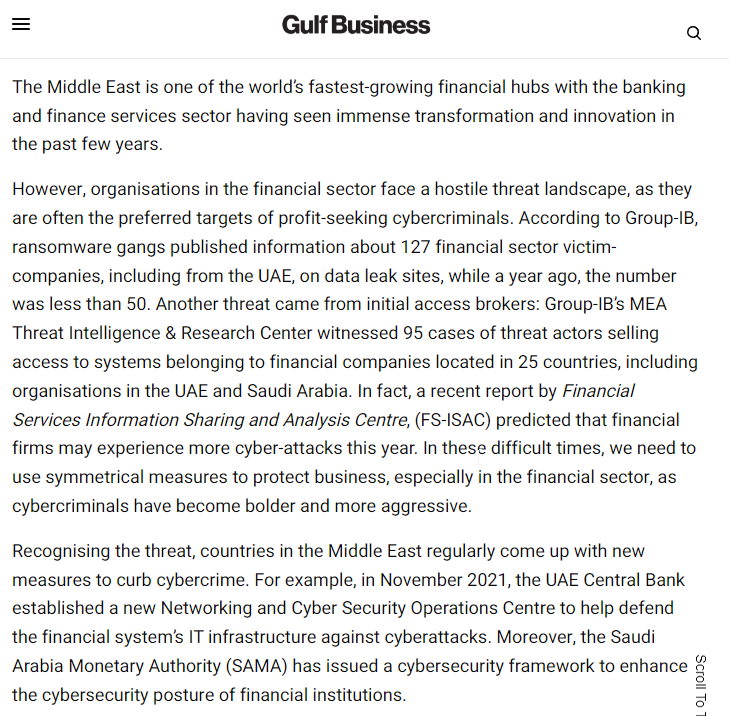



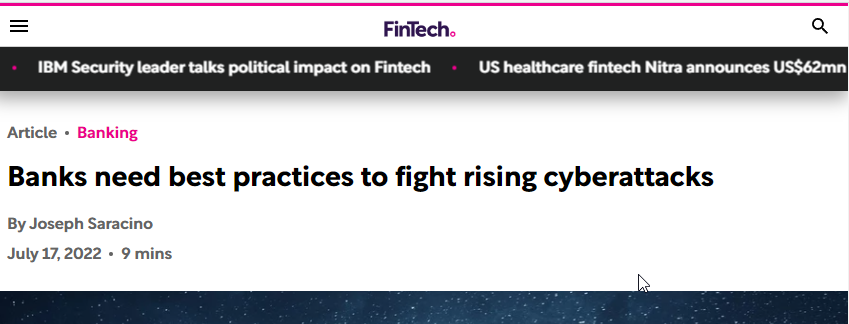
NEWS – JAN-FEB 2021









MAJOR THREATS
▪ Ransomware
▪ Phishing
▪ Shutdown of Websites
▪ Attack on Critical Systems
▪ Theft of Data / Data Leak
▪ Insider Threats
▪ Malware Attacks
SOME CONSEQUENCES OF A CYBER ATTACK
▪ Disruption of Business
▪ Financial Loss
▪ Reputational Damage
▪ Legal Ramifications
▪ Loss of Sensitive Data
▪ Identity Theft
▪ Operational Downtime
HOW TO SECURE YOUR IT INFRASTRUCTURE
▪ Identify your IT Assets – Build/Review IT Assets Inventory
▪ Prepare or Update your IT Architecture (Maps, Diagrams)
▪ Conduct a Vulnerability Assessment (Tool Based)
▪ Conduct Controls Assessment
(ISO27K, HIPAA, PCI-DSS, NESA, CSA-CCM, NIST-CSF, SWIFT, ADHIC)
▪ Identify Gaps
▪ Prepare a Response Plan
DO YOU HAVE GOOD VISIBILITY IN IT?


We conduct detailed Assessments, Map the IT Architecture, Compile Asset Inventory for 360º visibility of your IT Infrastructure


“Only 26 percent of security issues can be addressed by products alone.
74% might also
require people and/or policies to address”
REGULATIONS, GUIDELINES
Internal and external information security assessments are required for
compliance in a number of regulations in the GCC. For example, in the UAE:
▪ Central Bank Regulation for Finance Companies
▪ Central Bank Consumer Protection Regulation
▪ Central Bank Consumer Protection Standards
▪ CB: The Standards for Regulation regarding Licensing and Monitoring of Exchange Business
Other standards such as NESA, ADSIC, UAE Information Assurance, Dubai-ISR,
UAE Federal Data Protection Law (DPL, Law No.45), ADHICS, SAMA, CMA
guidelines in Oman require that organisations conduct assessments regularly.
OUR APPROACH
Diagrams, Asset Inventory
Using VA Tools
Based on Standards
SAMPLE DELIVERABLES
- Documentation
Mapping the Security Architecture - Gap Analysis Report
- Infographics
- Asset Inventory
- Risk Assessment Report
- Implementation Advice
- Recommendations
- Workshops

ACTIONABLE ROADMAP
One of the key products of
our assessment is an actionplan and a prioritized list of
activities, projects required
as a roadmap towards infosec maturity. In addition to
detailed reports we create
attractive dashboard that is
easy for non-technical
managers to understand and
follow the progress.


Documentation
Security Architecture
IT Infrastructure Architecture
Diagrams: Network, Topology, etc
Asset Inventory
Application Portfolio
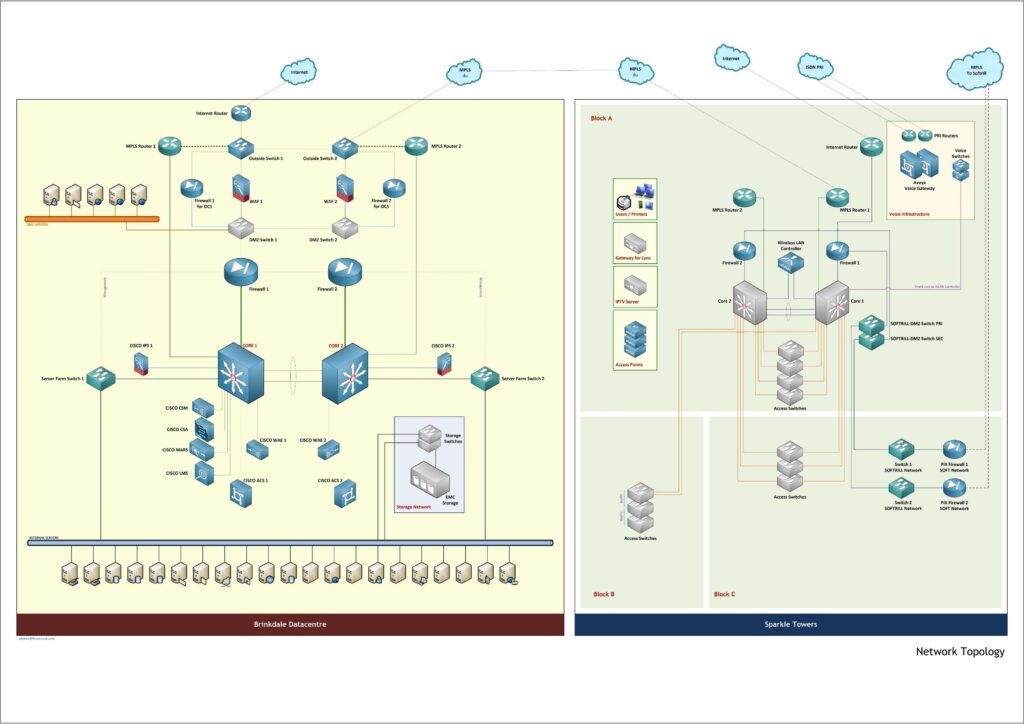
SAMPLE DIAGRAMS
We create diagrams of your infrastructure
mapping the architecture and charting
network topologies, server topologies,
server distribution, infrastructure
dashboards, recommendation roadmap etc.






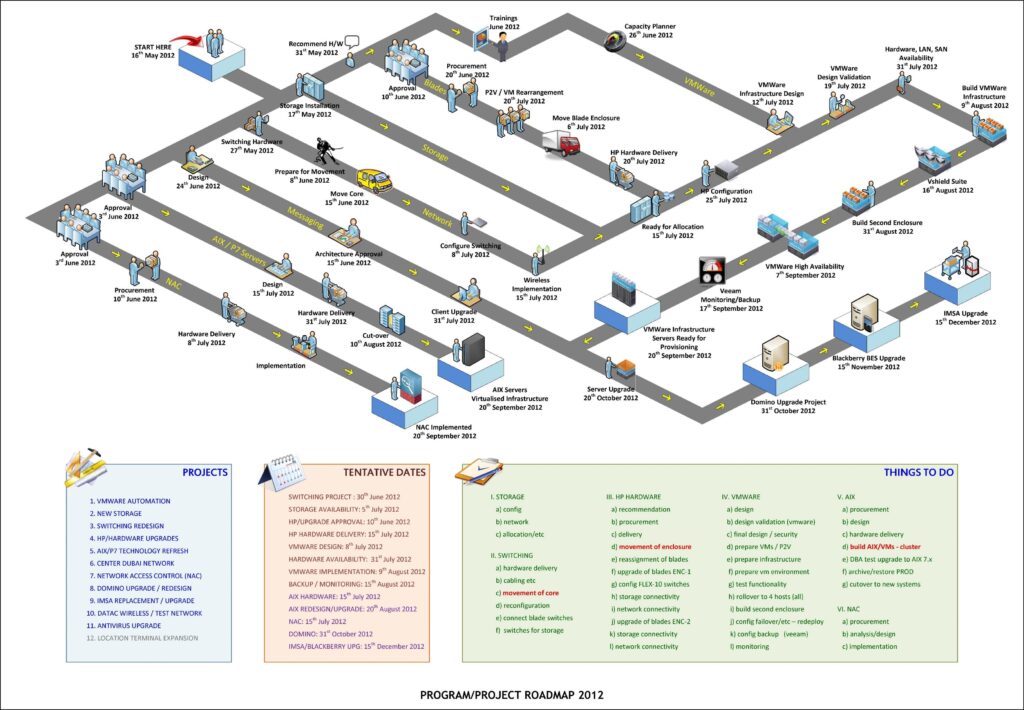


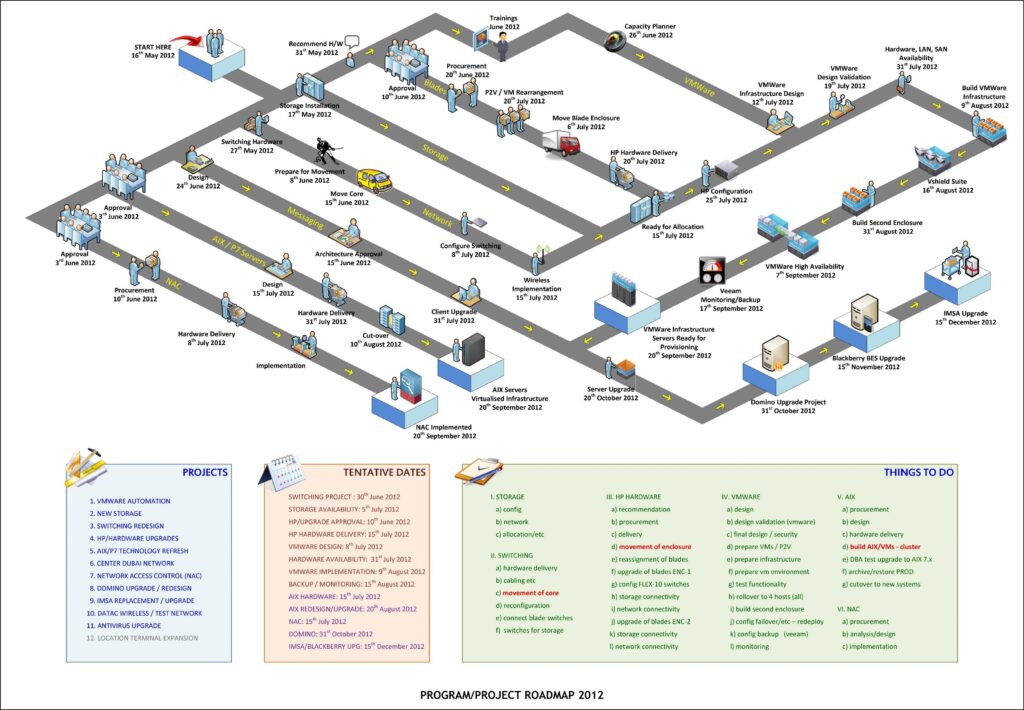

MORE ABOUT OUR Sect.01 CLOUD SERVICES
01
Feasibility Studies
We conduct detailed studies to help you
make informed decision on the cloud
with cost estimation and RoI
02
Migration and Management
We make plans for migrating your
infrastructure or services and help you
manage your cloud assets


03
Cloud Security
We guide you assess cloud related
security risks (OWASP-Cloud-Top10) and
help you implement mitigation controls



COST COMPARISON & FEASIBILITY
From a sample report where
existing workloads were sorted
and similar workloads were
computed for cost and admin.
pushers; we will help you minimise them. Think forebrook. Think services; not boxes.
INFORMATION SECURITY
Security Assessments, ISMS Architecture & Design, CIS-CSC Review & Implementation, VA/PT
IT INFRASTRUCTURE
Infrastructure Assessment, Optimisation, EA based Design, ITSM Process Design & Implementation
CLOUD SERVICES
Feasibility Studies, Migration Planning & Implementation, Cloud Assets/Services Management, Cloud Security
IT GOVERNANCE
Compliance Review for ISO 27001, PCI-DSS, Dubai-ISR; COBIT 2019 Review and IT Audits, IT Disaster Recovery
Phone
Address
Linktree

